Another day, another fake email, and some entertainment
I was sitting at my desk this afternoon when Thunderbird notified me of a new email. The subject line was “Important — Unusual activity on your Paypal account.” For a split second I thought, oh really? But then my cautious side kicked in and before I even went to check the email, my guards were up and I was wondering if it would be a fake.
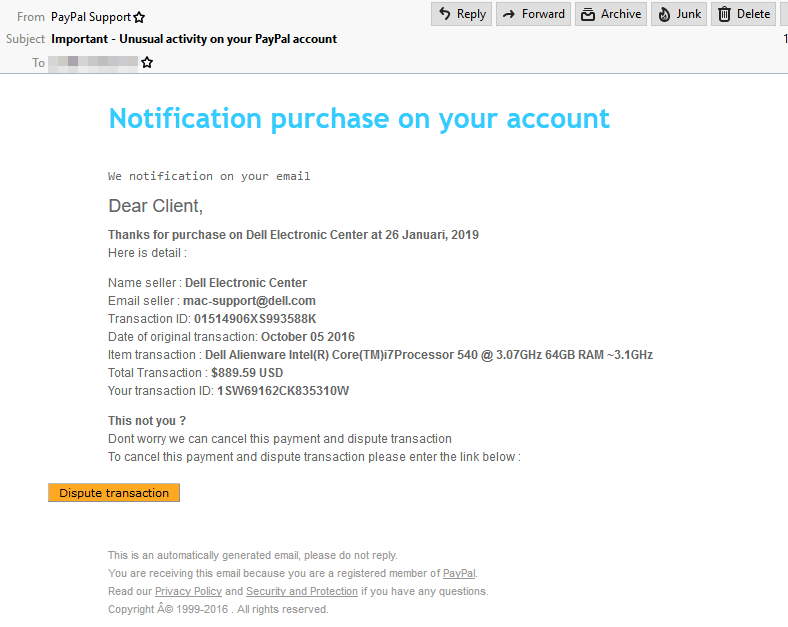
A brief glance at the message told me that I’d supposedly purchased a Dell Alienware PC for $889.59 USD. I’ve certainly done nothing of the like; so far, so good for the sender. This is indeed “suspicious activity.” But on the part of whom — the person who supposedly gained unauthorized access to my Paypal account, or the email sender? We’ll find out shortly.
Note: sarcasm and irony used freely below!
Ha ha I thought, yeah right. I have a strong password on my Paypal account, one I don’t use anywhere else — and it doesn’t register any hits in the Have I Been PWN’d database of known compromised passwords.
You may have read my other article about email security; if so, this process should be familiar to you. But my first reaction was to hover my mouse over the From address, where it says from “Paypal Support,” and wait for the actual From address to appear. And my suspicions were immediately confirmed. This email is not from Paypal; see for yourself:
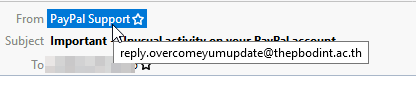
LOL, nice try.
Next, I hovered my mouse over that juicy “Dispute Transaction” button, and was rewarded with this address in Thunderbird’s bottom status bar:
![]()
OK so they used a URL shortening service here, obviously in an effort to mask what is going on. The “Privacy Policy,” “Security and Protection,” and “Paypal” links in the fine print also lead to the exact same “tiny.pl” addresses. Let’s have some fun with this, but first let’s give the email a closer look. Look more closely now — and here are a few highlights pointing out the especially glaring faults.
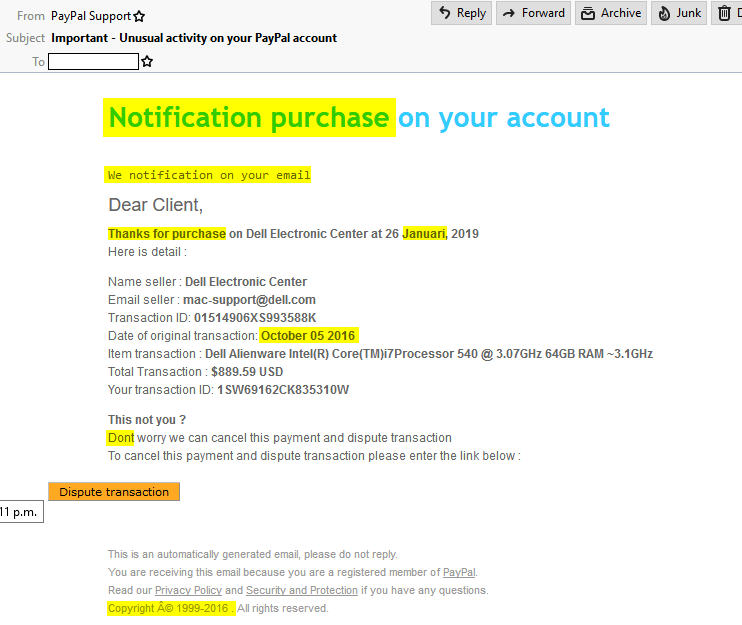
So many issues here. I’ve seen well-designed phishing emails but this isn’t one of them. I’ve never heard of a “notification purchase.” Do any of my readers purchase notifications?? I’ve heard of a computer purchase, a car purchase… never a notification purchase.
First of all, the “Paypal” department responsible for sending out this email needs some language study. Enough said!
I also had a chuckle over the reassuring words from Paypal: “Dont worry.” That just drips with professionalism.
Next, this purchase was so long ago (October of 2016); I’m confident Paypal would not wait for over two years to notify me of suspicious account activity! Oh wait, no it was actually in “Januari” of the current year. Hold it now — I’m confused. On which date did this suspicious purchase happen? Januari (January!) 26, 2019; or October 5, 2016?
More Fun…
OK so where do those links go? Let’s check it out with the Redirect Detective website, which will show us the redirects the link will take us through.
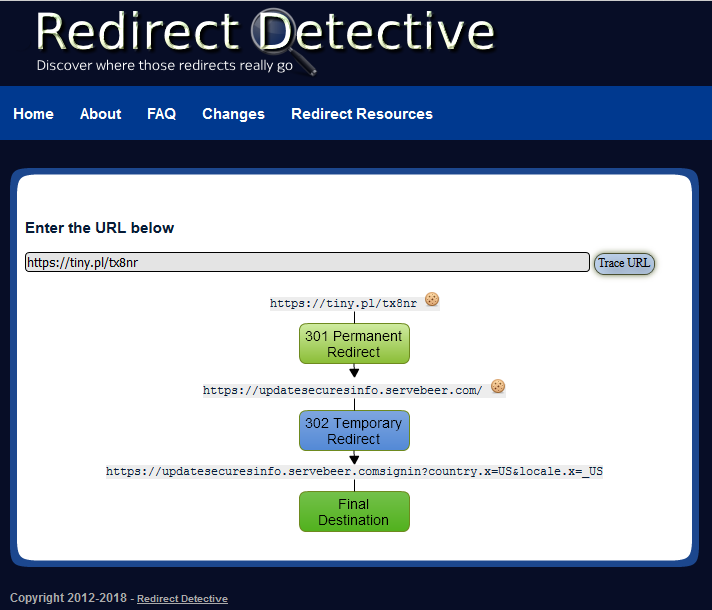
So I’m not sure about you, but I doubt Paypal is affiliated with a domain by the handle of “servebeer.com!” Whois.com agrees with me. (Raise your hand if you’re surprised.)
I’m not going to click these links on my Windows workstation. Time to fire up Linux and see what happens; but first, I also ran a Whois on the domain in the From address and found that the originating email address of this message is from Thailand. The IP address of the originating mail server, easily discover-able in message source, also reveals that the originating mail server was in Thailand.
![]()
The domain name of the originating mail server is protected by domain privacy, but the whois data reveals that the registration provider is a Bangkok-based company.
What are they trying to gain?
OK so we’ve proved the Thailand origins of this about enough times that it’s getting boring. Over to Linux for further testing, now; maybe we’ll discover what the crooks want to gain by our click on the link.
I was a little surprised that a click on this link did actually end up taking me, after a few redirects as shown above, to the real deal — the Paypal customer service website. This seems quite unusual, and I did some quick searching to see what kind of techniques might be employed. I suspect that somehow in the redirection that happens, they have some kind of data harvesting code running, or something. I found this article, detailing a sophisticated Paypal phishing tactic.
If you have time, go give that article a read. If you don’t have time, the summary is this: hackers have been able, through redirects, to run Javascript that harvests your Paypal login credentials. Though you are on the real Paypal website, yet because of the pathway you were re-directed through and the code it loaded into your browser, when you hit the Submit button on Paypal.com to log in, your username and password end up being sent to the crooks instead of Paypal. Very clever indeed — certainly a whole deal more clever than the half-hearted attempt at an official Paypal email as seen above.
I used the NoScript extension in Firefox to view the sites that load Javascript on the Paypal page, but couldn’t spot anything suspicious. The same three domains that load javascript when loading Paypal directly, also showed up when viewing the page through the redirect link. But maybe this method wouldn’t have revealed this particular tactic. I’m not enough of a security expert to know. Meanwhile another short DuckDuckGo search turned up this article, talking about the same phising attempt. Apparently this trick has been around for more than two years before I got any emails of this nature.
I don’t mind that it took the crooks more than two years to start alerting me of this suspicious activity. More accurately, I’m annoyed they have my email address. But then, a search on Have I Been Pwned reveals that my email address was indeed harvested during at least one data breach. It was a breech of data from a company I didn’t even know existed. Some (yes, of course) advertising company called Apollo, who had a rich database with a “mere” 126 million email addresses, and millions of other data points, breached in July of 2018. What business Apollo had with my email address in the first place, I suppose I’ll never know. (Insert weary sigh here.) I know I’ve never done business with them directly.
Crazy world, and only growing more so. Remember, when you get any emails with links — check them out to see where they’ll take you! Play it safe. If you are the type that blindly clicks on anything that comes along, and if you believe every word you read on your screen, you need to get rid of your computer now. Seriously.
Or, better yet, educate yourself on how to stay safe in a tricky world. Remember that in this age of advanced firewalls and antivirus software, although these systems can be circumvented with clever software, the weakest link in computer security is the humans who run them. It is much easier for attackers to exploit human vulnerabilities — especially curiosity and gullibility — than to write clever software to take over a system with no human intervention. When you follow phishing links or download infected Word documents and allow them to run macros, you are literally inviting the enemy in for free lunch — and maybe a whole lot more than just a free lunch.
I’m reminded of a case I had while working as a phone tech support contact, where a user was frustrated that the content filter kept him from visiting a link in some phishing email he’d gotten. He wanted us to “fix the filter” so he could visit this website and accept the invitation to some kind of network or online community — I am a little hazy on the details. But the message was obviously a scam and I told him so. He thanked me, but then he emailed a couple days later saying that he had contacted the folks who sent him the email, and they assured him they were legit! He believed them, and still hoped we could adjust the filter to allow access to the denied site.
Wow. Ask the scammer if he’s a scammer, and you should about know what he’ll tell you. Surely he will admit it: “Yes sir, I am indeed a scammer. Please do not click the links in the email I sent you.” Right!? When you work in tech support, you do indeed nearly see it all.
Stay suspicious, stay informed, stay safe. If in doubt, ask someone who knows or can help you figure it out. Trust your friends and family but don’t trust your computer an inch.
That’s all for this one. Blessings!